WELCOME
Insights, tutorials, and stories to explore the world of cybersecurity and digital threats.
Latest Posts
New Zero-Day Exploited in the Wild Targets VMware Tools and Aria Operations
There’s a new vulnerability making waves in the VMware ecosystem, and it’s not just theoretical. A China-linked threat group known as UNC5174 has been caught exploiting a zero-day privilege escalation…
The Oldest Trick Still Works: Why Password Cracking Is Beating Your Defenses in 2025
Every year, security teams gear up to defend against the latest wave of zero-days, advanced persistent threats, and nation-state malware. But while we’re busy preparing for cyberwarfare, attackers are walking…
When Hackers Patch Your Servers: The Strange Case of CVE-2023-46604
It’s not often you see a cyberattack that ends with the attacker installing security updates. But that’s exactly what’s happening in the latest wave of Apache ActiveMQ exploits, and it’s…
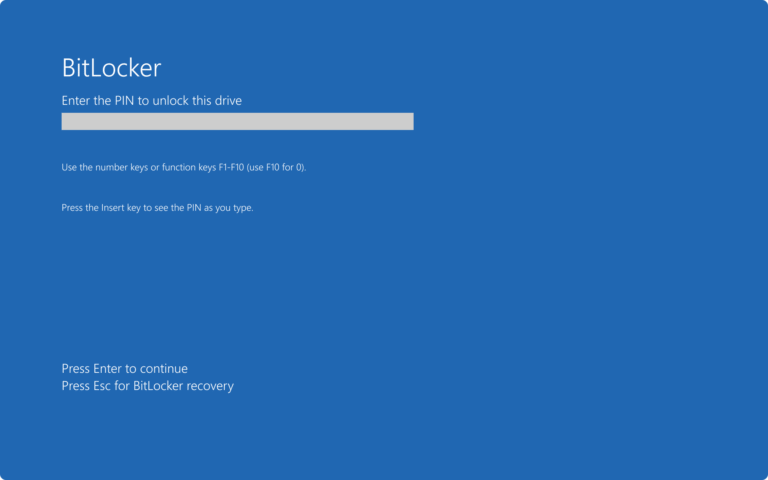
Bypassing BitLocker: How WinRE Zero-Days Turn Encryption into Illusion
BitLocker has always been Microsoft’s flagship defense against stolen-device data theft. You enable it, and your laptop’s hard drive becomes an unreadable vault without your key or password. At least,…
SharePoint Under Attack: CVE-2025-53770 and the Key That Opens Every Door
Microsoft SharePoint is the backbone of collaboration for thousands of enterprises, document libraries, internal portals, team sites. On-premises versions run on ASP.NET/IIS, and like any web app, they need a…